Think of managed IT security services as your own dedicated, outsourced team of cybersecurity specialists. They’re on watch 24/7, proactively monitoring, managing, and defending your business’s digital footprint. It’s a massive step up from only fixing things after they break, offering round-the-clock protection for a straightforward monthly cost. For a lot of businesses, it’s simply the smartest way to get access to top-tier skills and enterprise-grade security tools.
Why East Midlands Businesses Need Proactive Cyber Defence
Picture this: your Nottingham logistics firm or Leicester manufacturing plant grinds to a halt because of a cyber-attack. This isn’t some far-off news story; it’s a real and present danger for businesses right here in the East Midlands.
The old IT model of ‘break-fix’ is a recipe for disaster when threats are this constant and clever. Your in-house team is likely already snowed under with day-to-day tasks, which can leave dangerous gaps in your security.
This is where managed IT security services completely change the game. It’s like hiring a specialist firm to build, staff, and guard a high-tech fortress around your entire digital operation. Instead of scrambling to react to a breach, this model gives you a dedicated 24/7 cyber defence team whose sole focus is stopping incidents before they can cause any real damage. They’re there to protect your data, your systems, and your hard-earned reputation.
Shifting from Reactive to Proactive Security
The real difference is in the mindset. A reactive approach means you’re waiting for an alarm bell—a virus warning, an employee reporting a dodgy email—before you do anything. By that point, the damage could already be done.
Proactive defence is all about constant vigilance.
A proactive security posture means anticipating threats, continuously monitoring for vulnerabilities, and actively hunting for malicious activity. It’s about staying one step ahead of attackers, not just cleaning up after them.
Making this shift isn’t just a good idea; it’s a necessity for any business wanting to thrive today. This is especially true for small and mid-sized enterprises (SMEs) that don’t have the budget for a full-time, in-house security department staffed with certified experts.
The Growing Demand for Expert Protection
The need for this kind of specialist protection is driving huge market growth. In the UK alone, the managed services sector was valued at £15.35 billion in 2023 and is on track to hit a staggering £28.29 billion by 2032.
This explosion is fuelled by the relentless wave of cyber threats hitting businesses of all sizes, particularly in regions like the East Midlands where SMEs are embracing digital technology more than ever.
Outsourcing your security isn’t just about handing off a few tasks. It’s about bringing on a strategic partner who is genuinely invested in keeping your business resilient. By taking on board some practical cybersecurity tips for small businesses, East Midlands businesses can build a solid foundation. When you combine that knowledge with expert managed services, you create a truly powerful defence.
The Building Blocks of a Modern Security Service
When you bring a managed IT security partner on board, you’re not just buying a single piece of software. You’re investing in a complete, multi-layered defence system for your entire business.
Think of it like securing your office premises. You wouldn’t just rely on a single lock on the front door, would you? Of course not. You’d have CCTV, a decent alarm system, and maybe even reinforced windows, all working together to keep unwanted visitors out.
In the digital world, this layered approach is even more crucial. A proper security service is built from several core components, each designed to protect a different part of your business from different kinds of threats. Exploring a guide to managed network security solutions can give you a deeper understanding of how these pieces fit together.
This layered defence strategy is all about protecting the things that matter most: your data, the systems you rely on to operate, and your hard-earned reputation.
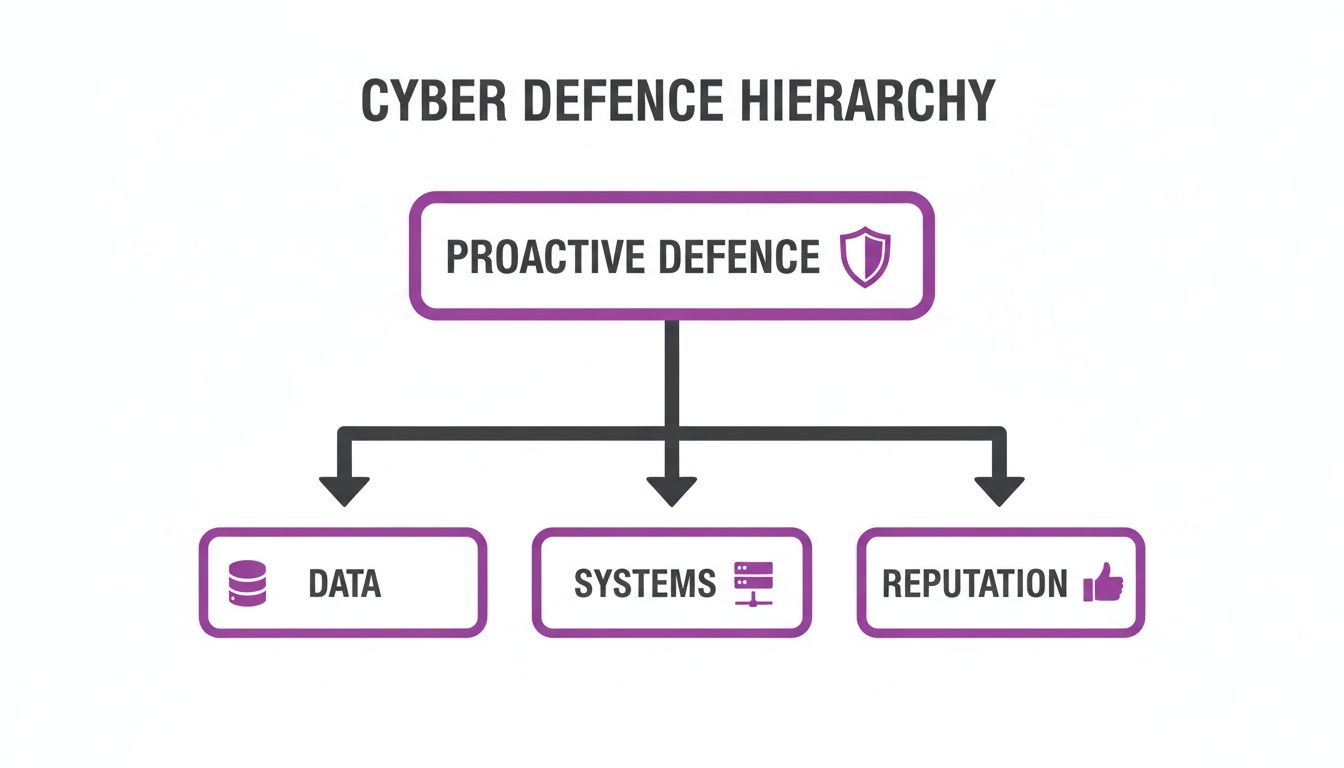
So, what are these essential building blocks? Let’s break them down into what they actually do for your business.
Core Managed Security Services and Their Business Benefits
To get a clearer picture, this table shows the key services that form the foundation of a robust security posture, what they deliver, and why they’re so important.
| Security Service | What It Delivers | Why It’s Critical for Your Business |
|---|---|---|
| SIEM & MDR | Centralised threat monitoring (SIEM) and an expert team for active threat hunting and response (MDR). | Provides 24/7 eyes on your network, catching suspicious activity an in-house team might miss and actively neutralising threats before they cause damage. |
| Endpoint Protection | Advanced security for all user devices (laptops, PCs, mobiles), going far beyond traditional antivirus. | Secures your most vulnerable entry points, stopping malware and unauthorised access on the devices your team uses every day. |
| Patch Management | Automated, consistent updates and security patches for all your software and operating systems. | Closes the security holes that cybercriminals love to exploit, preventing breaches caused by known vulnerabilities. |
| Backup & Disaster Recovery (BDR) | A complete, tested plan for data backup and rapid restoration of your entire IT environment after a crisis. | Ensures you can get back up and running quickly after a ransomware attack or system failure, minimising downtime and financial loss. |
These services aren't just separate tools; they're interlocking parts of a cohesive strategy designed to keep your business safe and resilient. Let's look a little closer at how some of them work.
The Brains of the Operation: SIEM and MDR
At the very heart of any modern security setup, you’ll find two critical technologies working in tandem: Security Information and Event Management (SIEM) and Managed Detection and Response (MDR). Think of them as the central nervous system of your entire defence.
A SIEM platform is your digital command centre. It pulls in log data from every corner of your network—servers, firewalls, applications, and user devices—and analyses it all in one place. By spotting unusual patterns or strange behaviour, it flags potential threats that would otherwise fly completely under the radar.
But an alert is just a signal. That's where MDR comes in. If SIEM is the alarm system, the MDR service is the expert security team that immediately investigates the incident. They hunt for hidden threats, figure out what’s happening, and take decisive action to shut the attack down. It's the difference between a siren blaring and having a professional response team on-site in minutes.
Securing Every Connection Point
Every laptop, tablet, and mobile phone your team uses is a potential doorway into your network, making them prime targets for attackers. This is why robust Endpoint Protection is non-negotiable.
Modern endpoint security isn’t just about antivirus anymore. It uses sophisticated techniques to block advanced malware, prevent unauthorised access, and automatically isolate a compromised device to stop an infection from spreading like wildfire through your network. With so many East Midlands businesses supporting remote or hybrid working, strong endpoint protection services are absolutely essential for securing your new, expanded perimeter.
Another vital—and often neglected—layer is Patch Management. Software developers are constantly finding and fixing security holes in their products. Failing to apply these patches quickly is like leaving the back door unlocked for cybercriminals. A managed service takes this headache away, ensuring all your systems, from your servers to your Microsoft 365 apps, are consistently updated and secured against the latest known threats.
Building Resilience with Backup and Recovery
Even with the best defences in the world, the unthinkable can still happen. A clever ransomware attack or a critical hardware failure could grind your entire operation to a halt. This is why a comprehensive Backup and Disaster Recovery (BDR) plan is one of the most fundamental building blocks of security.
A solid BDR strategy isn't just about having copies of your files. It's about having a tested, reliable plan to restore your entire IT environment quickly and efficiently, ensuring business continuity with minimal disruption.
The constant threat of cyber-attacks has fuelled a massive demand for managed IT security services across the UK. In fact, by 2025, the UK is projected to have 12,867 managed service providers, with 22% of them focusing specifically on cyber security. For mid-sized businesses and charities across the East Midlands—from a logistics firm in Derby to a non-profit in Lincoln—this expertise is becoming essential. Without it, how can an already busy IT team hope to keep up?
Getting to Grips with Service Models and Pricing
Trying to make sense of proposals and price lists for managed IT security can feel like you're learning a new language. But getting your head around the different ways providers work and how they charge is the key to making a confident, smart decision for your business. It all boils down to choosing the right level of partnership.
And that decision has never been more important. The UK's Managed Service Provider (MSP) sector is a booming market, set to hit a milestone in 2025 with 12,867 active providers generating a staggering £51 billion in revenue. A recent government report also showed that while cloud computing is the most common service, a significant 22% of these providers focus specifically on cyber security. It’s a clear sign of how vital these services have become. You can dig into the full managed service providers market research for more detail.
Finding the Right Service Model
No two businesses are the same, and neither are their security needs. That's why most providers offer a few different models to fit your internal setup and what you're trying to achieve.
-
Fully Managed Services: Think of this as the complete, hands-off approach. The provider takes full ownership of your security, handling everything from 24/7 monitoring and threat hunting to incident response. It's the perfect fit for a business that doesn't have its own dedicated IT security team.
-
Co-Managed Services (Co-MITs): This is all about partnership. Your in-house IT team works alongside the provider, creating a powerful hybrid. Your team can handle the day-to-day stuff, while the provider brings specialist tools, round-the-clock monitoring, and expert backup. It’s a great option for organisations in places like Lincoln or Scunthorpe that have good IT people but need to add some serious security firepower.
-
Project-Based Services: Sometimes, you just need an expert for a one-off job. This could be a security audit, help with a compliance check, or rolling out a new security system. Project work lets you bring in the specialists you need for a specific task without a long-term contract.
Understanding Common Pricing Structures
Once you know the kind of relationship you want, the next piece of the puzzle is figuring out how you’ll pay for it. The good news is that pricing for managed IT security is usually designed to be predictable, which makes budgeting a whole lot easier.
Here are the most common ways it’s structured:
-
Per-User, Per-Month: This is probably the most popular model out there. You pay a simple, flat monthly fee for each person in your company. It’s easy to follow and scales up or down as your team changes. In the UK, you can expect this to be anywhere from £25 to £100 per user per month, depending on how many services are included.
-
Per-Device, Per-Month: This works just like the per-user model, but your cost is tied to the number of devices you're protecting—like servers, laptops, and firewalls. This can be a smart move if you have lots of staff sharing a smaller pool of equipment.
-
Tiered Packages: Many providers bundle their services into packages, often labelled something like Bronze, Silver, and Gold. Each tier adds more services and a higher level of protection. This makes it really straightforward to pick a pre-set bundle that lines up with your security needs and budget.
The Importance of the Service Level Agreement
Of all the paperwork involved, the most important document you’ll sign is the Service Level Agreement (SLA). This is your contract. It spells out, in black and white, exactly what the provider is promising to deliver.
An SLA is much more than just a legal document; it’s your guarantee of quality. It sets out the specific, measurable standards the provider has to meet, making sure they are truly accountable for protecting your business.
When you're looking over an SLA, zoom in on these key details:
- Response Time: How fast will they jump on a security alert? For anything critical, this should be a matter of minutes, not hours.
- Resolution Time: What’s their target for actually fixing the problem? This shows you how committed they are to getting you back to normal with minimal disruption.
- System Uptime: This is a promise of availability, usually shown as a percentage like 99.9% uptime, which ensures your most important systems stay online.
- Reporting Frequency: The SLA should state exactly how often you'll get performance reports, so you always have a clear view of the work being done to keep you safe.
A solid, transparent SLA removes any guesswork. It gives you the confidence of knowing your security partner is contractually bound to deliver when it counts.
How to Choose the Right Security Partner in the East Midlands
Picking a partner to handle your managed IT security is one of the biggest calls you’ll make for your business. The technology itself is vital, of course, but it’s the team you choose to manage it that really dictates how well you’ll stand up to cyber threats. This isn't about finding just another remote helpdesk; it's about finding a team that genuinely takes ownership of your security.
For businesses across the East Midlands, from growing companies in Newark to established firms in Grimsby, the right partner feels like an extension of your own team. They get the local business environment and are truly invested in your success. Finding that perfect fit means looking beyond a price list to properly weigh up a provider's expertise, responsiveness, and how well they click with your organisation's culture.
Local Presence and On-Site Support
While a lot of cyber security work can be done remotely, you can't beat having an expert who can be physically on-site when you really need them. A provider with a solid local presence in the East Midlands can offer hands-on support during a critical incident or for more complex projects that need a personal touch.
That local connection means they’re not just a faceless company on the other side of the country. They understand the regional landscape and can provide a level of personal service that's impossible to replicate from a distance. This is especially important when you’re building long-term trust and a true partnership. To see how this local approach makes a difference, check out the benefits of dedicated managed IT support in Nottingham.
Deep Expertise in the Microsoft Ecosystem
Let's face it, most businesses today run on Microsoft. Your security partner absolutely must have deep, proven expertise within this specific ecosystem, covering everything from Microsoft 365 to Azure. They should know how to get the most out of the native security features built into these platforms and how to blend them seamlessly with their own advanced tools.
Look for key certifications that prove they know their stuff.
- Microsoft Solutions Partner: This title shows the provider has met Microsoft’s tough standards for technical skill and successful customer projects.
- Cyber Essentials / Cyber Essentials Plus: These UK government-backed certifications show a commitment to the fundamentals of cyber security, protecting against the most common online threats.
A partner with this level of specialisation can make sure your investment in Microsoft is not only productive but properly locked down.
Verifying Their Incident Response Process
When a security breach happens, every second is critical. A vague promise to "deal with it" just won't cut it. You need to ask potential partners to walk you through their specific incident response (IR) plan. A mature provider will have a clear, documented process that they can share with you.
A robust incident response plan isn't just a process; it's a commitment. It outlines exactly who does what, when, and how, ensuring a calm, controlled, and effective reaction when you are most vulnerable.
Ask them direct questions. What are their communication protocols? What does their escalation procedure look like? How do they analyse an incident afterwards to stop it from happening again? Their answers will tell you everything you need to know about how prepared they are to act decisively under pressure.
Choosing the right partner is a detailed process that involves asking the right questions. We've put together a checklist to guide you through this evaluation.
Checklist for Selecting Your Managed Security Partner
A practical guide to help East Midlands businesses compare and choose the best managed security provider for their unique needs.
| Evaluation Criteria | Key Questions to Ask | Why This Matters |
|---|---|---|
| Local Presence & Support | Are you based in the East Midlands? Can you provide on-site support in an emergency? | Local teams understand regional challenges and can provide faster, hands-on help during a crisis. |
| Technical Expertise | Can you show us your Microsoft certifications? What experience do you have in our industry? | Certifications prove expertise. Industry-specific knowledge means they understand your unique risks and compliance needs. |
| Incident Response Plan | Can you walk us through your step-by-step incident response process? What is your guaranteed response time? | A clear, tested plan is the difference between controlled recovery and chaos. Vague answers are a major red flag. |
| Service Level Agreement (SLA) | What specific response times, uptime, and reporting metrics are included in your SLA? | The SLA is your contract. It must clearly define expectations and guarantee the level of service you’re paying for. |
| Client Testimonials & Fit | Can we speak to some of your current clients, ideally in our area or sector? | Talking to existing customers provides honest, unfiltered feedback on their real-world performance and reliability. |
| Cultural Alignment | How do you communicate technical issues to non-technical staff? | You need a partner who speaks plain English and works collaboratively. A good cultural fit builds trust and a better long-term relationship. |
This checklist isn't exhaustive, but it provides a solid foundation for your discussions. The goal is to find a partner who not only has the technical skills but also aligns with your business values and communication style.
Reviewing Testimonials and Cultural Fit
Finally, look for social proof and think about the human element. Ask to see case studies or, even better, ask to speak with some of their current clients—especially those in the East Midlands or in a similar industry to yours. Hearing directly from other businesses gives you invaluable insight into a provider's reliability and the quality of their service.
Beyond their technical skills, think about the cultural fit. Do they communicate clearly, without hiding behind jargon? Do they listen to your concerns and seem genuinely interested in what you're trying to achieve as a business? The best security partnerships are built on transparency, clear communication, and mutual respect. You're trusting them with one of your most valuable assets—make sure they’re a team you can truly work with.
The Onboarding Journey and Measuring Your Return
So, you’ve signed on the dotted line for managed IT security services. What now? A great partnership hinges on a smooth, well-planned onboarding process. This isn't about just flipping a switch; it's a carefully orchestrated journey to get you protected from day one with minimal disruption.
The whole point is to transition your business seamlessly from its current state to a fully defended environment. Your team shouldn't have to deal with downtime or frustrating teething problems. The process is typically broken down into several clear, common-sense phases.
The Phased Approach to Onboarding
Any professional provider worth their salt will have a tried-and-tested roadmap for getting their services integrated. This makes sure nothing gets missed and that your new security posture is built on solid foundations.
-
Discovery and Assessment: This is where we get to know your world inside and out. The security partner dives deep into your current IT environment, identifying every device, application, and data source. They’ll map your network, check your existing security controls, and start pinpointing potential weak spots.
-
Strategic Planning: Armed with the insights from the discovery phase, a bespoke security plan is drawn up. This isn't a one-size-fits-all document. It’s a specific roadmap outlining which tools will be used, how they’ll be configured for your business, and the rules of engagement for monitoring and incident response.
-
Deployment and Integration: Now for the technical bit. Agents are carefully installed on endpoints, logging systems are plugged into the central SIEM platform, and monitoring is switched on. It’s a meticulous process, done with care to ensure full visibility without getting in the way of your day-to-day operations.
-
Tuning and Optimisation: In the first few weeks, the system gets fine-tuned. The security team works to weed out "false positives"—those harmless activities that can sometimes look suspicious. The goal is to make sure that when an alert goes off, it's a real threat that needs immediate attention.
-
Transition to Continuous Monitoring: Once the system is stable and dialled in, it moves into the 24/7 monitoring phase. At this point, your business is officially under the watchful eye of the provider’s Security Operations Centre (SOC), and your onboarding is complete.
Measuring Your Return on Investment
It's great to have peace of mind, but the value of managed IT security can also be measured in pounds and pence. Proving this Return on Investment (ROI) is key to justifying the spend to the board or your leadership team.
The true ROI of managed security isn't just about the attacks you stop; it's about the business value you create. This includes protecting revenue, enabling productivity, and avoiding the crippling costs associated with a breach.
Thinking about it this way helps frame the service as a strategic investment, not just another line on the expense sheet.
Quantifiable Benefits for Your Business
Let's get down to brass tacks. Calculating the ROI involves looking at both cost avoidance and efficiency gains.
- Reduced Downtime Costs: Every hour your systems are down costs you money in lost revenue and staff productivity. If a security service prevents just one major incident a year, the savings can easily eclipse the annual cost of the service.
- Avoiding Specialist Recruitment Costs: Let's be honest, hiring, training, and keeping a team of in-house cybersecurity experts is incredibly expensive. Senior analyst salaries often push past £60,000 plus benefits. Outsourcing gives you access to a full team of specialists for a fraction of that.
- Improved Team Productivity: When your internal IT team is freed from constantly putting out fires and chasing security alerts, they can focus on projects that actually move the business forward. This shift from reactive support to proactive innovation is where real value lies.
- Lowered Compliance and Insurance Costs: Having a robust, professionally managed security posture looks great to insurers and can lead to lower cyber insurance premiums. It also drastically cuts the risk of eye-watering fines for non-compliance with regulations like GDPR.
By tracking these metrics, you can build a powerful business case. To get started with a formal evaluation, it helps to use an established framework. For a structured approach, you can learn more by exploring our Request for Proposal (RFP) template for IT services, which helps you ask the right questions from the very beginning.
Ready to Secure Your Business? Here's Your Next Step
We’ve covered a lot of ground in this guide, from the realities of modern cyber threats to the specific services that keep businesses safe. If there's one key takeaway, it's this: proactive, layered security isn't a 'nice-to-have' anymore. It's an absolute necessity. And having a local partner who genuinely understands your business is the difference between simply having tools and having a true defence.
For over 25 years, we at F1Group have been on the ground, working with businesses right here in the East Midlands. We've built our reputation by combining that local presence with certified, in-depth expertise in the Microsoft technologies you already use every day. It's this blend that lets us provide the hands-on, accountable support you need to feel confident and in control.
Your Local Microsoft Security Experts
Choosing F1Group isn't just about outsourcing your security; it's about gaining a local partner who's also a specialist in the Microsoft ecosystem. We know the challenges facing businesses in Nottingham, Lincoln, Leicester, and the surrounding areas because we're part of the same community. Our entire focus is on turning complex security jargon into practical, effective solutions that actually work for your specific business.
We're here to build a real relationship, one based on trust and results you can see. You don't just get a service ticket number; you get a dedicated security ally who is genuinely invested in seeing your business thrive, securely.
The worst time to think about security is after an attack. The best time is right now. Making a proactive move today is the single most important investment you can make in the future of your business.
Protecting your organisation is a massive responsibility, but you don't have to carry it alone. The right partner makes robust security achievable and sustainable, freeing you up to focus on what you're best at—running your company. Let us handle the complexities so you can have the peace of mind that comes from knowing you're properly protected by a team of local experts.
It’s time to move forward.
Protect your data. Empower your team. Secure your future.
Give us a call on 0845 855 0000 or send us a message to start the conversation. Let's talk about how we can safeguard your business together.
Frequently Asked Questions About Managed IT Security
Even after getting a good overview of managed IT security, it's natural to have questions about what it all looks like day-to-day. We've pulled together some of the most common queries we hear from business leaders across the East Midlands to give you a clearer picture.
Is My Business Too Small for Managed Security?
We hear this a lot, but the answer is a definite no. In fact, it’s often the small and mid-sized businesses that get the most out of a managed security service. Cybercriminals love targeting smaller companies, banking on the assumption that their defences will be easier to crack.
Modern managed security services are built to scale. Most providers use a straightforward per-user monthly fee, so you're only ever paying for what you actually use. This model gives an SME in Derby access to the exact same level of enterprise-grade security tools and expertise as a massive corporation, but at a price that makes sense for their budget.
How Does This Integrate with Our Microsoft 365 Setup?
An excellent and critical question, especially since so many of us run our businesses on Microsoft's platform. A good security partner won't just bolt another system on top of what you already have. They should integrate directly into your Microsoft 365 and Azure environments to strengthen them from the inside out.
They take the security features you already have and enhance them, layering on advanced threat monitoring and expert management that simply isn't there out of the box. The result is a single, seamless security posture where your investment in Microsoft technology is both productive and properly protected.
Think of a skilled managed security provider as an extension of your own team. Their job is to use their deep expertise to unlock the full security potential of the tools you already own and rely on every day.
What Happens If We Do Get Breached?
This is the big one. Even with the best defences in the world, no one can guarantee 100% protection. The real measure of a security partner is what they do when the worst happens. If a breach occurs, your provider immediately kicks off a well-rehearsed Incident Response (IR) plan.
This isn't a panic-stricken scramble; it's a calm, methodical process led by people who have been here before.
- Containment: The absolute first priority is to isolate the affected systems. This stops the threat in its tracks and prevents it from spreading further across your network.
- Eradication: Once contained, the team gets to work hunting down and completely removing the threat from your environment.
- Recovery: With the threat gone, they begin restoring affected systems from clean backups to get your operations back online as quickly and safely as possible.
- Analysis: After the dust settles, a full analysis is carried out. The goal is to figure out exactly how the breach happened and put stronger measures in place to make sure it can't happen again.
This rapid, expert-led response is designed to minimise damage, slash downtime, and get your business back to work.
Your business deserves the best protection. At F1Group, our local team of certified experts is ready to provide the hands-on, accountable security your organisation needs to operate with confidence.
Phone 0845 855 0000 today or send us a message to discuss how we can secure your business's future.

