Privileged Identity Management, or PIM, is all about controlling, monitoring, and locking down the accounts that have powerful access to your company’s most important systems. Think of these accounts—like your IT administrator or senior leadership logins—as the digital ‘master keys’ to your entire business. They’re a massive target for cyber attackers who want to get their hands on your data.
Securing Your Digital Keys to the Kingdom
Picture a physical key cabinet in your office. Inside are the keys to everything: the server room, the finance office, the HR filing cabinets. You wouldn’t just leave that cabinet unlocked, would you? PIM is the smart, automated security guard standing watch over your digital key cabinet. It makes sure keys are only given out when someone has a legitimate reason, only for as long as they need it, and their access is logged.
This is a world away from the old way of doing things, where administrators had permanent, ‘always-on’ high-level access. PIM is built on the principle of ‘least privilege’. This simply means people get just enough access to do their specific task, and only when they need it. It’s a powerful, proactive way to defend against both hackers trying to get in and threats that might come from inside.
The Escalating Risk of Unchecked Privileges
Leaving powerful accounts unsecured isn’t just a theoretical risk; it’s a real and present danger for UK businesses. A shocking 74% of data breaches begin with a privileged account being compromised. On top of that, 34% of all identity-related breaches in the last two years specifically went after these high-value accounts. Protecting your business means understanding the full scope of digital threats, which is covered well in this Cyber Security for Business and Risk Management Guide.
This isn’t just an IT problem. Managers and business owners themselves make up 25% of all cybercrime victims in the UK. For businesses here in the East Midlands, that statistic should be a wake-up call. Too many employees have permissions that go far beyond what their job actually requires, creating a huge, unnecessary security gap. To get a better handle on the bigger picture, you can explore the concepts in our article on what is privileged access management.
A solid PIM strategy is built on a few core pillars, each designed to tighten your security and give you more control.
Core Components of a PIM Strategy
| PIM Component | Core Function | Business Benefit |
|---|---|---|
| Just-in-Time (JIT) Access | Grants elevated permissions temporarily, only for the duration of a specific task. | Reduces the window of opportunity for attackers. Privileged access isn’t sitting idle. |
| Approval Workflows | Requires a manager or another admin to approve a request for elevated access. | Adds a human checkpoint to prevent unauthorised or mistaken access escalation. |
| Role-Based Activation | Users activate a pre-approved role when needed, rather than having it permanently assigned. | Ensures access is intentional and justified, creating a clear audit trail for every use. |
| Time-Bound Access | Sets an automatic expiry time for any elevated permissions, removing them after the task is done. | Eliminates the risk of ‘privilege creep’ where users accumulate unnecessary access over time. |
| Auditing & Reporting | Logs every request, approval, and action taken while a user has elevated privileges. | Provides complete visibility for security reviews, compliance checks, and incident investigation. |
By bringing these components together, you get a system that protects your most critical assets without getting in the way of day-to-day work.
By implementing a robust PIM strategy, you fundamentally shrink your organisation’s ‘attack surface.’ This makes it significantly harder for cybercriminals to move through your network even if they manage to compromise a standard user account.
Getting to grips with Privileged Identity Management is the first real step towards building a more resilient business. It’s not just an IT tick-box exercise; it’s a fundamental business practice for protecting what matters most.
How Privileged Identity Management Works in Practice
Privileged Identity Management isn’t some abstract security theory; it’s a practical, hands-on system with clear, automated rules. Instead of permanently handing out the ‘keys to the kingdom’, PIM breaks down high-level access into four core, manageable steps. These principles work together to grant powerful permissions securely, but only when they’re genuinely needed.
At its core, PIM shifts your security posture from a risky state of ‘always-on’ privilege to a much safer ‘on-demand’ model. This simple change dramatically reduces the chance of a compromised account causing widespread damage, because powerful permissions are no longer left active and unattended.
The diagram below gives you a simplified look at how PIM acts as a gatekeeper for your critical data.
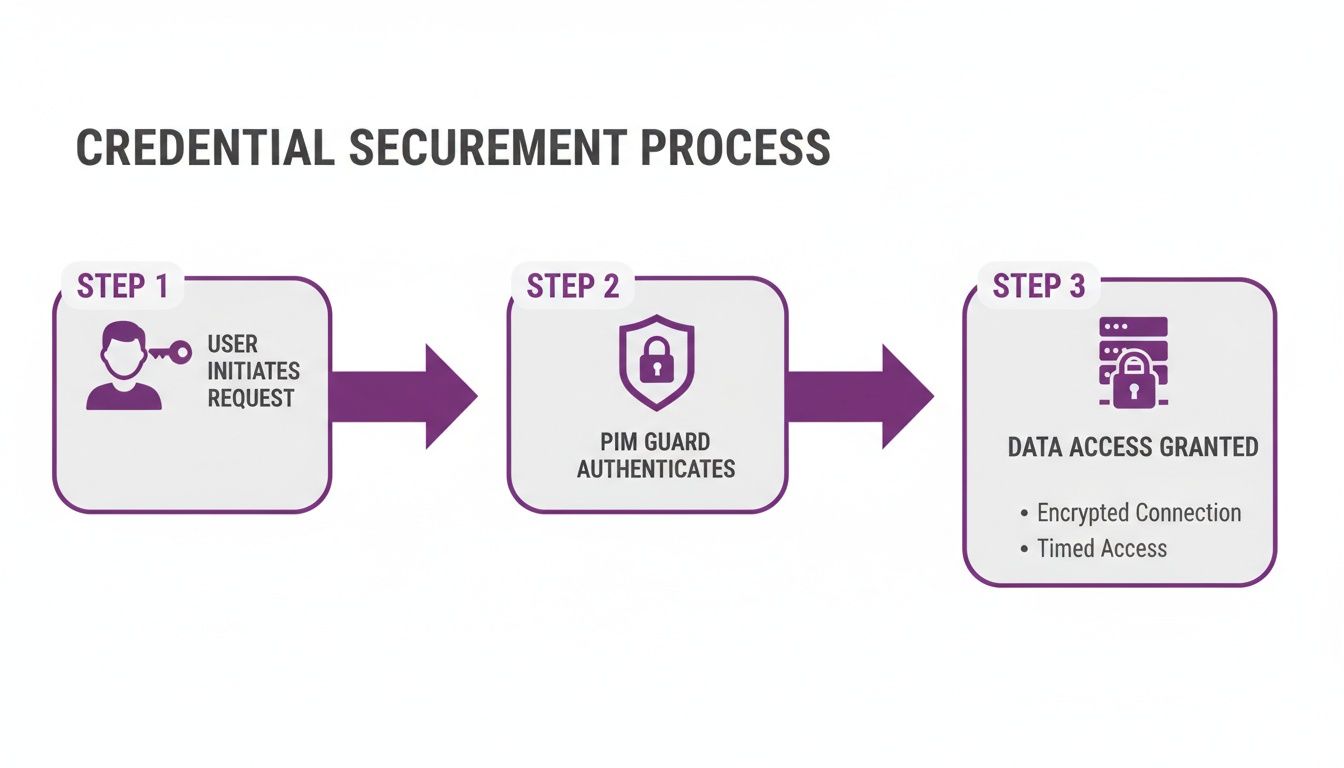
This process makes sure no one gets direct, unchecked access to sensitive systems. It adds a crucial verification step every single time someone needs to perform an administrative task. Let’s dig into the key functions that make this happen.
Just-in-Time Access and Approval Workflows
The first and most important idea is Just-in-Time (JIT) access. Think of it like a bank vault. You can’t just walk in; you need a specific reason, and a manager has to turn their key. In the same way, an IT administrator in Leicester needing to update a critical server doesn’t have permanent admin rights. They must first request temporary elevation through the PIM system, explaining what they need to do and why.
This request kicks off an Approval Workflow. A notification is automatically fired off to their manager or another designated approver. Only once that approval is given does the system temporarily elevate the user’s permissions. This human checkpoint stops unauthorised access in its tracks and ensures every privileged action has a clear business justification, aligning perfectly with the broader principles we explain in our guide on what is identity and access management.
Time-Bound Elevation and Auditing
Once access is approved, it isn’t a free-for-all. Time-Bound Elevation ensures the permissions are only active for a limited, pre-defined period—say, for one hour. When that time is up, the privileges are automatically revoked, and the user’s account returns to its normal, non-privileged state. This completely gets rid of the common security risk of “privilege creep,” where people slowly collect more and more access over time.
Finally, everything is recorded. Comprehensive Auditing creates a detailed, unchangeable log of the entire process:
- Who requested access.
- When it was requested and approved.
- What justification they provided.
- How long the elevated access lasted.
This detailed audit trail is gold dust for security reviews, compliance checks, or for investigating any suspicious activity. It gives you complete transparency, showing you exactly who is accessing your company’s digital crown jewels and why.
Why Your East Midlands Business Needs PIM
For any growing business in the East Midlands, getting to grips with Privileged Identity Management is no longer a job just for the IT department—it’s a fundamental business priority. Adopting PIM isn’t about ticking a box; it brings real, practical benefits that protect your operations, your reputation, and ultimately, your bottom line. It’s about shifting from simply reacting to security problems to actively preventing them.
The first and most obvious win is shrinking your ‘attack surface’. Think of every permanent administrator account as an unlocked door to your business. Cybercriminals are always looking for these open doors. By using Just-in-Time access, PIM makes sure these doors are only opened for a specific, approved reason and are locked again the moment the job is done. This drastically cuts down the chances of a breach.
This tight control is vital for stopping both external attacks and internal threats. Whether it’s a disgruntled employee acting maliciously or a well-meaning team member who makes a costly mistake, PIM adds a crucial safety net. It guarantees that powerful permissions are never used without a good reason and a clear, traceable record.
Strengthening Your GDPR Compliance
If you’re running a business in Lincoln, Nottingham, or anywhere in the UK, you know that GDPR compliance isn’t optional. PIM is a fantastic tool for helping you meet these obligations by enforcing the ‘principle of least privilege’—a cornerstone of the regulation. In simple terms, this principle means people should only have access to the data they absolutely need to do their job, and nothing more.
PIM helps put this principle into practice automatically. It gives you a structured, easy-to-audit system that proves you’re taking real steps to restrict access to sensitive personal data. This isn’t just about dodging hefty fines; it’s about building trust with your customers and showing you take their data privacy seriously.
Keeping Pace with a Growing Threat Landscape
The numbers don’t lie. The UK’s Privileged Identity Management market was valued at £455 million and is expected to explode to a staggering £1.36 billion by 2035. This massive growth is being fuelled by the relentless rise in cyber threats and tougher regulations that demand rock-solid protection for privileged accounts. You can find out more about these UK market trends on Market Research Future.
By giving you a transparent, real-time view of who can access what, PIM enhances your operational oversight. It transforms privileged access from a hidden risk into a managed, visible, and controlled business process.
At the end of the day, for any forward-thinking East Midlands business, putting PIM in place is a strategic investment in your company’s resilience. It protects your most important digital assets, helps you stay compliant, and gives you the clarity you need to operate safely. It’s a core building block of modern cyber security.
Ready to secure your business’s most critical access points?
Phone 0845 855 0000 today or Send us a message to discuss how we can help.
Implementing PIM with Microsoft 365 and Azure
If your business is already running on the Microsoft ecosystem, the path to locking down your most sensitive accounts is more straightforward than you might think. Microsoft’s own solution, Azure AD Privileged Identity Management (PIM), is designed specifically to secure, control, and monitor high-level access across your organisation, and it plugs directly into your existing setup.

This isn’t some third-party tool you have to awkwardly bolt on. PIM is built right into Azure Active Directory (now called Microsoft Entra ID), the very same identity service that powers Microsoft 365.
This tight integration is a game-changer. It means you can use PIM to manage admin roles not just in Azure itself, but across your entire Microsoft 365 world, including Exchange Online, SharePoint, and even Dynamics 365. To get a better handle on the backbone of all this, you can read our deep-dive on what is Azure Active Directory here.
Understanding the Licensing Requirements
One of the first questions we always get from businesses is about the cost. The good news is that you don’t need to buy PIM as a separate, expensive product. It’s already included as a feature within certain Microsoft licence plans, making it incredibly cost-effective for companies already using Microsoft 365.
Generally, you’ll need an Azure AD Premium P2 licence for anyone who will be managing PIM or requesting elevated access through it. This specific licence is also bundled into the more comprehensive plans like Enterprise Mobility + Security (EMS) E5 and Microsoft 365 E5.
By simply making use of the tools baked into higher-tier Microsoft 365 plans, you can roll out a world-class PIM strategy without needing to budget for entirely new software.
This approach lets IT managers and business owners get more value from their existing tech stack, transforming a standard subscription into a powerful security shield.
Microsoft 365 and Azure PIM Licensing
To give you a clearer idea of the investment, let’s break down the common licence plans that include Azure PIM. While exact pricing can fluctuate, this table provides a practical overview for budgeting and planning.
| Licence Plan | Includes Azure AD PIM? | Ideal For | Estimated Monthly Cost (GBP per user) |
|---|---|---|---|
| Azure AD Premium P2 | Yes | Organisations needing advanced identity protection just for their key admin users. | Around £7.50 |
| Microsoft 365 E5 | Yes | Larger businesses wanting the full suite of security, compliance, and analytics tools. | Around £53.80 |
| EMS + Security E5 | Yes | Companies focused on a top-tier security and mobility management solution. | Around £13.70 |
For many businesses we work with across the East Midlands, the most practical route is often assigning an Azure AD Premium P2 licence to a handful of IT administrators. It’s a surprisingly affordable way to secure your entire digital estate, putting enterprise-grade security well within reach of small and medium-sized businesses.
Ready to figure out the best licensing for your team? Give us a call on 0845 855 0000 today or send us a message to talk it through.
PIM Implementation Best Practices
Getting a Privileged Identity Management rollout right is about much more than just flicking a switch on a new piece of tech. It’s about building a solid, practical strategy from the ground up. For businesses here in Nottingham, Scunthorpe, and across the East Midlands, a proper PIM implementation is the key to creating a security shield that actually works.
It all starts with knowing what you’ve got. You need to begin with a comprehensive ‘privilege discovery’ audit to map out every single account in your organisation that holds any kind of elevated access. We’re talking about the obvious ones, like your IT administrators, but also the less obvious ones—think finance managers with special permissions in your accounting software, or marketing staff with admin rights to your CRM.

Defining Roles and Workflows
Once you have a clear picture of who holds the keys, the next job is to define what those keys are for. Every privileged role needs a documented purpose, making sure that access is tied directly to a specific job function. This simple step is your best defence against “privilege creep”—that all-too-common situation where staff slowly accumulate unnecessary permissions over time.
With roles clearly defined, you can then build approval workflows that make sense for your day-to-day operations. A workflow could be straightforward, perhaps requiring a single manager’s sign-off for temporary access. For your most critical systems, however, it might need a more robust, multi-step approval process. The goal is to add that essential human checkpoint without grinding productivity to a halt.
A critical part of long-term PIM success is establishing a regular access review cycle. At least quarterly, you should review all privileged roles to ensure they are still necessary, removing any that are no longer required.
Strengthening Your Defences
Finally, remember that PIM shouldn’t operate in a vacuum. It’s at its most powerful when it’s layered with other security controls, and the most important partner it has is Multi-Factor Authentication (MFA).
By enforcing MFA for any user activating a privileged role, you add an absolutely vital layer of verification. It makes life incredibly difficult for an attacker trying to use stolen credentials, because they won’t just need the password; they’ll also need that second authentication factor to get anywhere.
Following these best practices turns PIM from a simple tool into a core part of your security culture. A trusted partner like F1Group can guide you through each step, making sure your PIM strategy is effective, efficient, and fits your business perfectly.
To start building your PIM strategy, give us a call on 0845 855 0000 today or Send us a message.
Frequently Asked Questions About PIM
Even with a clear plan, it’s natural for questions to pop up when you’re exploring something like Privileged Identity Management. Here are the answers to some of the most common queries we get from business owners and IT managers across the East Midlands.
What Is the Difference Between PIM and Standard Access Management?
Think of standard access management—often called Identity and Access Management (IAM)—as the bouncer at the main door of a club. Its job is to check IDs and make sure only people on the guest list get in. It controls who has basic access to what; for example, ensuring the sales team can access the CRM, but not the finance system.
Privileged Identity Management (PIM) is like the special security detail that guards the VIP lounge. It’s a focused security layer that deals only with the accounts that hold the master keys—your administrators and other ‘super-users’. PIM adds crucial extra checks like temporary access, approval workflows, and detailed auditing specifically for these high-risk accounts, which standard IAM simply isn’t designed to do.
Where Should a Small Business Start with PIM?
For any small or medium-sized business, the first step is always the same: a ‘privilege discovery’ audit. You can’t secure what you don’t know you have. This means methodically identifying every single account across your entire organisation that has administrative or elevated permissions.
It’s easy to think this just means your main IT administrator, but the scope is much wider. You need to find the admin accounts for your finance software, your CRM, your cloud services, and any other system where someone holds powerful rights. Pinpointing exactly who holds the ‘keys to the kingdom’ is the absolute foundation for getting them secured.
PIM transforms privileged access from an invisible, constant risk into a visible, managed, and controlled business process. It brings accountability to your most powerful accounts.
How Can We Measure the Success of a PIM Implementation?
Thankfully, you don’t have to guess if PIM is working. The results are tangible and can be tracked with clear metrics that show a real improvement in your security posture.
A successful PIM rollout can be measured by looking for:
- A sharp drop in the number of permanent admin accounts. The goal is to shift as many as you can to an on-demand, just-in-time model.
- Faster, more reliable de-provisioning of access when someone leaves the company. This closes the door on dangerous ‘orphan’ accounts with high-level privileges.
- The ability to generate a complete audit trail for any privileged activity at a moment’s notice. This is invaluable for compliance checks and security incident investigations.
Ultimately, the biggest measure of success is the one you don’t see—the prevention of a security breach that could have been caused by a compromised super-user account.
Protecting your business starts with securing your most powerful accounts. To discuss how PIM can work for your organisation, speak with one of our experts.
Let F1Group Help Secure Your Privileged Access
Protecting accounts with high-level access isn’t just another item on your IT to-do list; it’s one of the most vital steps you can take to secure your entire business. Leaving these “keys to the kingdom” unguarded is a massive risk, especially as cyber threats get smarter and regulations become stricter. You’ve now got a handle on what Privileged Identity Management is, but the real challenge is putting it into practice effectively.
That’s where we come in. As a local IT partner right here in the East Midlands, F1Group has spent years working with Microsoft’s security tools. We get the unique pressures that businesses in our region face – the constant balancing act between managing costs and staying ahead of security threats. We can help you build and run a solid PIM strategy that actually fits the way you work.
Your Local PIM Experts
It doesn’t matter what industry you’re in; the need for tighter control over powerful accounts is universal. Take the finance and insurance sectors, for example. They’re leading the charge in adopting PIM in the UK, driven by the absolute necessity of protecting sensitive financial data under GDPR.
This isn’t just a concern for big banks. If your East Midlands business uses tools like Dynamics 365, this trend is a major wake-up call, especially when you consider that a staggering 90% of UK financial organisations have been hit by security breaches. You can dig deeper into these trends over at Data Bridge Market Research.
Let us help you lock down your digital crown jewels. Our goal is to give you peace of mind by making sure your most powerful accounts are protected, all without getting in the way of your team’s day-to-day work.
Don’t wait for a security breach to make this a priority. It’s time to be proactive and protect the assets that matter most.
Ready to take the next step? Get in touch with F1Group to talk it through.
Phone 0845 855 0000 today or Send us a message.